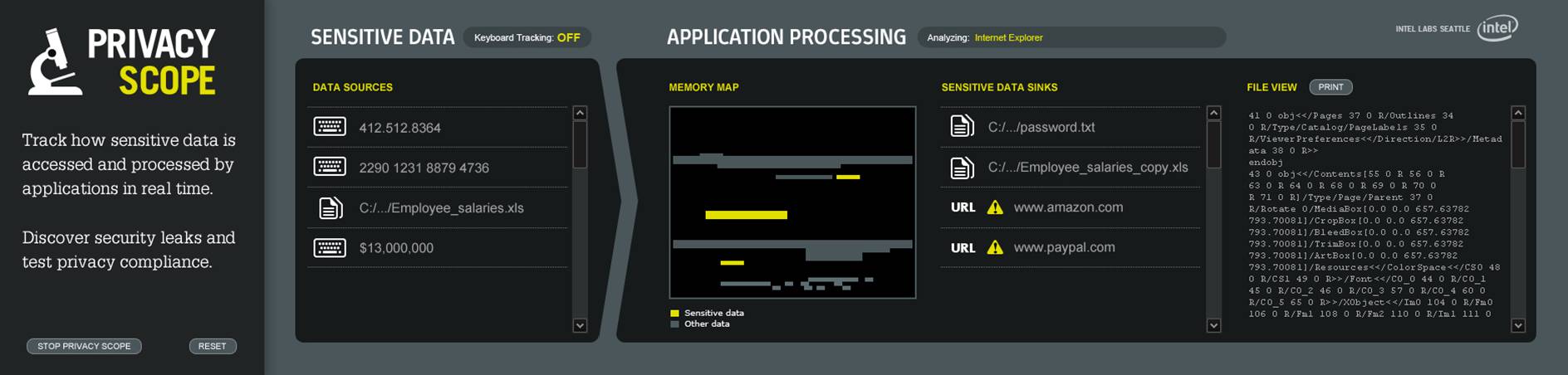
Discoverying leaks is difficult because applications encrypt, compress, or transform data internally. Privacy Scope leverages dynamic taint analysis technique for precise information flow tracking:
- Instruments application's instructions using Intel's Pin dynamic binary translator.
- Implements optimization techniques for reducing performance overhead of taint-tracking.
- Interposes system calls for tracking keystrokes, files, and network activities.
Privacy Scope runs on Windows XP and is successfully tested with real applications including Windows Notepad, Internet Explorer, and Yahoo! Messenger. To build our system, we developed and integrated a set of techniqu3s that include: mixed instruction and function-level tainting; function summaries for efficiency and accuracy of applicaiton-only tainting; special semantics for corner-case instructions and kernel side-effects; and tainting on demand rather than at load time. The result is a comprehensive system that is efficient enough to track where sensitive information goes in large multi-threaded network applications. See our paper for detailed microbenchmarking results and an application study.